A variety of methods can deliver information across an enterprise, including ad hoc and on-demand reports, dashboards, and analytics capabilities.
Most data warehouse environments offer users a variety of information sources. Architectures can contain data staging areas, operational data stores, enterprise data warehouse database(s), data marts, and other data store types. Each of these stores offers different opportunities for information investigation and delivery depending on the point in time and state of the data. In many cases, all information delivery has been redeployed to the data warehouse environment to offload the transactional systems allowing these systems to focus on business processing, not delivery. This redeployment has become more practical as data transformation processing transitioned from a slow monthly or overnight activity to intra-day or near real time. This provides users with the opportunity to analyze cleansed and integrated data for making both tactical and strategic business decisions.
There are varieties of components that need to be assembled to produce an integrated information delivery framework for users. To accommodate the variety of information sources and user functional needs, an enterprise portal is used to distribute and manage applications. The portal provides a single gateway to information regardless of the data source and application. It provides for personalization and security applicable to the user’s functional business needs and their role in the organization. Some delivery components may not be available or visible to a user depending on their security. In addition, a variety of web enabled delivery components through a single portal will complete the framework.
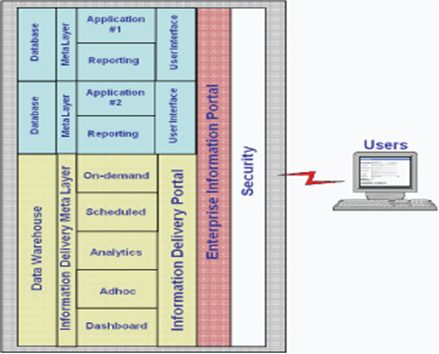
Figure 1 – Information Delivery Framework
The first component is an on-demand reporting capability. This component allows authorized users to request information from the operational or analytical data stores on their own as needed. Standard reports are organized by category and made available through this component. Once a user selects a particular report, they are prompted for filtering criteria (metadata) to limit data content. Additionally, optional columns can be selected for inclusion in the report in order to meet the business information needs. All report categories, prompt values, filters, sort options, graphs, and optional column selections are personalized based on the role and content (row) security the user has in the organization. Processing of the final report is done real time, typically in minutes, against the selected data store. Results can be saved to personal folders or converted to alternate formats (e.g., spreadsheet) for further analysis. Typically, all managers and other leaders in the organization have access to this component limited by security (role-based).
The second component is a subscription reporting capability. This component delivers standard operational or analysis reports to the users on a scheduled basis. These are reports that typically do not change in format or content. They may be reports that are best run during off- peak periods due to the amount of processing time required to produce them. The users have no choices to make concerning content or format of the report. Security for the particular user is automatically applied during runtime based on their role and content security parameters. The user simply subscribes to the report for a specified period (e.g., year) and selects how often they wish to receive it. Reporting processing occurs as a batch cycle during off peak hours in order to maximize resource utilization. Notification of new reports or subscription renewals is done through this component. Results can also be saved to personal folders or alternate data formats. All management would have access to this component.
The third component is the analytics capability. This component allows the user to identify and explore trends in the information through multidimensional analysis. This can be accomplished through online analytical processing (OLAP) either using relational database (ROLAP) or multidimensional cubes (MOLAP) methods. Both methods allow the user to extract and analyze multiple characteristics of the business to compare against performance measurements. Analysis can initiate at a summarized level of information and, based on observed trends, allow users to drill down in detail to understand the source. Users have varied ability to make content or format changes to the result sets. Security is applied automatically based on the user role and content security. Processing occurs either online or in batch depending on the OLAP solution used. Results sets typically can be saved to personal folders or to alternate file formats. The analytics component usually is distributed to a limited set of management.
The fourth component is an ad-hoc reporting capability. This component allows specialized users in the organization to query a limited subset of operational and analytical data stores. These users are typically performing high variable data extracts, reports, or queries. To guard overall performance of the environment, governors exist that restrict data volume and processing time of requests. Access to control, security, and system tables is also restricted. The same role and content security found in the other components is applied to all queries. Processing occurs online and result sets can be saved locally or in alternate formats. Access to this component should be to a very limited set of users in an organization who have a comprehensive knowledge of the data and structure.
The fifth and final component of the framework is a dashboard. This consists as series graphical displays throughout the portal showing performance of key indicators, such as revenue, productivity, turnover, and other measures. Each dashboard display is customized based on the role and content security of the particular user. The dashboard display provides a linkage to other delivery components of the framework for further analysis and details.
Additional capabilities include a proxy function that allows users to assign their reporting privileges to designated peers or managers for a specified period. Other considerations for an information delivery framework include the use of a single sign on (SSO) product to allow users to authenticate against an entitlement store once and avoid repeated challenges across the delivery components. This is needed especially if the components are from different vendors.
Conclusion
Having this combination of components integrated through a portal enables an integrated delivery framework. This framework allows any organization to take advantage of the data stored in its data warehouse or other data storage solutions for integrated business intelligence and analytics.